My story begins at my day job, the company had some new equipment installed and so I received some training on it. The final part of the familiarization was what to do if you can fix it, at this point the instructor pointed out an eWON router:

“IT has said we can’t have it switched on all the time but if you get a failure we can dial in and check the systems remotely” I was immediately interested in this device, I could see it could log multiple devices, full I/O, Flash and full routing. It’s a remote fault finders dream! We weren’t given access to the device but I was extremely interested in its capabilities so like any skeleton worth his bone meal I headed to Shodan. Shodan is like a search engine but instead of pages, it looks for devices on the net.
A quick search later I found almost 4,000 devices, after accessing one of the many I found it to be password protected a few minutes later after finding the instruction manual I had the default user and pass and no surprise I was in.
The first thing I noticed was that I was the highest level user I could do just about anything to this device and like I had seen it had full I/O control over something complicated. None of that really concerned me I was only here for research of the device. Another thing that drew my attention was the file type:
xxx.xxx.xxx.xxx/Ast/MainAst.shtm
I’d never seen .shtm before and thought it might be something I look at later.
After this, I narrowed my search to my home country thinking that I’d like to be sure nothing else belonging to my work had anything like this that had been left with default creds. 140 devices in the UK, I had a quick look at one of them, default creds again and found myself on a very different page:
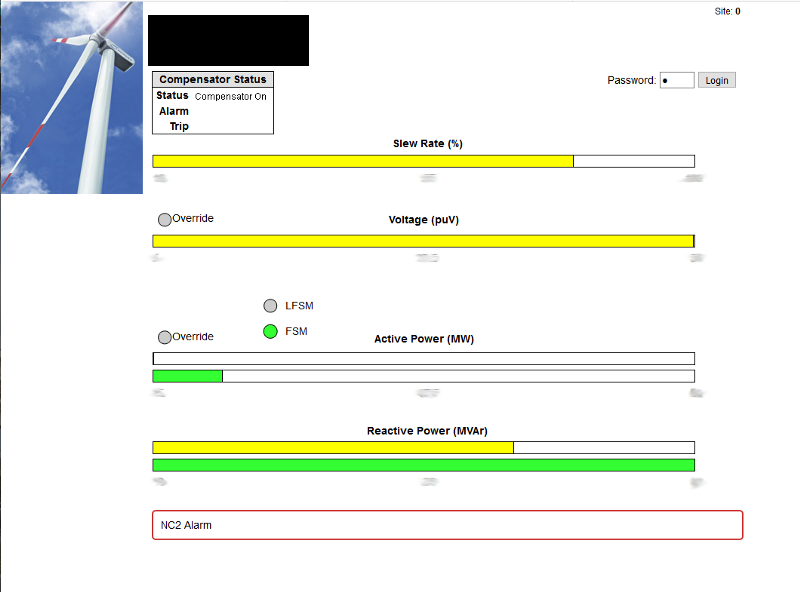
At first glance I thought must be one of those domestic turbines. It’s a read-only page so perhaps I can forgive the default creds and a login box at the top that I thought would lead to the config pages but actually I found makes the slew rate and other settings changeable on this page. So is this a custom eWON designed just for this? No, The eWON has FTP and if you upload pages you can serve them on its inbuilt webserver as the default. So if you’re stuck on this page xxx.xxx.xxx.xxx/usr/xxxxx/index.shtm how could you then configure the device? The answer is by browsing the original page mentioned earlier. This would have been difficult to enumerate but I already knew this was the default, so I have full control.
Ok, that’s pretty cool I thought. I don’t even need to log in the read-only page because I could edit the I/O here. That’s about when I noticed the power output, at a glance had thought domestic kW but was in fact MW! I know electricity and that’s a lot of it! Glancing back at Shodan the organization the IP is registered too is actually a well-known energy provider, and they have at least 5 other sites with the same setup!
The scale of this was starting to hit home, I quickly checked the output of the other turbines, a total of 253MW across 5 sites and the final one was showing site number 113!?! I’ve never dealt in MW so I thought maybe it’s not as bad as I thought? Perhaps I’m over exaggerating this. Maths! Maths will save me from a panic attack!
Nope. I calculated with these 5 sites I had control of enough power for 6.5% of the homes in my country. 5 sites with a possibility of at least another 108? Thankfully, its a drop in the ocean if I include industrial usage but still a major concern. I’ve even worked out scenarios where you could do harm to the turbines probably disabling them.
Amazed at what I’ve found, I try to find security contacts at the company’s involved… Nothing. I send emails to customer support… Nothing! A day or so later the country has a massive power cut due to “unforeseen circumstances” I’m going to prison, aren’t I? As a last resort, I contacted the NCSC, pretty sure this isn’t what they are for but it’s national infrastructure and I want to go on record. Guess there is still a chance I could get taken in for this.
More details emerged about the “Unforeseen circumstances” and what I’d found was not involved, thankfully. All that panic was for nothing, but it really hit home the scale of what I’d found. The NCSC was extremely helpful, once again I’m sure this isn’t what they are here for but they did deal with it and even increased my Hackerone rep for the tip-off.
At least 12 months have passed and to be honest, I had distanced myself from this incase something happened. Today I have checked all the addresses and can report that the message got through, all the sites are now properly password protected! Allowing me to finally talk about this out loud.
One response to “Infosec Story: My Close call!”
[…] I’ve said a lot in the review in the video but in short, I really like the Yubikeys, how they work and how easy they are for improving security. If you’ve ever had an issue with your accounts being phished or hacked, this is pretty cut-and-dry the solution to your problems. Easy to set up and easy to use, if I had my way this would be the new normal. If you’ve enjoyed this video and post you might like another infosec one. […]